Para realizar una captura de una traza de red es necesario ser administrador y ejecutar el comando
|
1 |
netsh trace start persistent=yes capture=yes tracefile=c:\fichero.etl |
Pasado un tiempo se para con el comando
|
1 |
netsh trace stop |
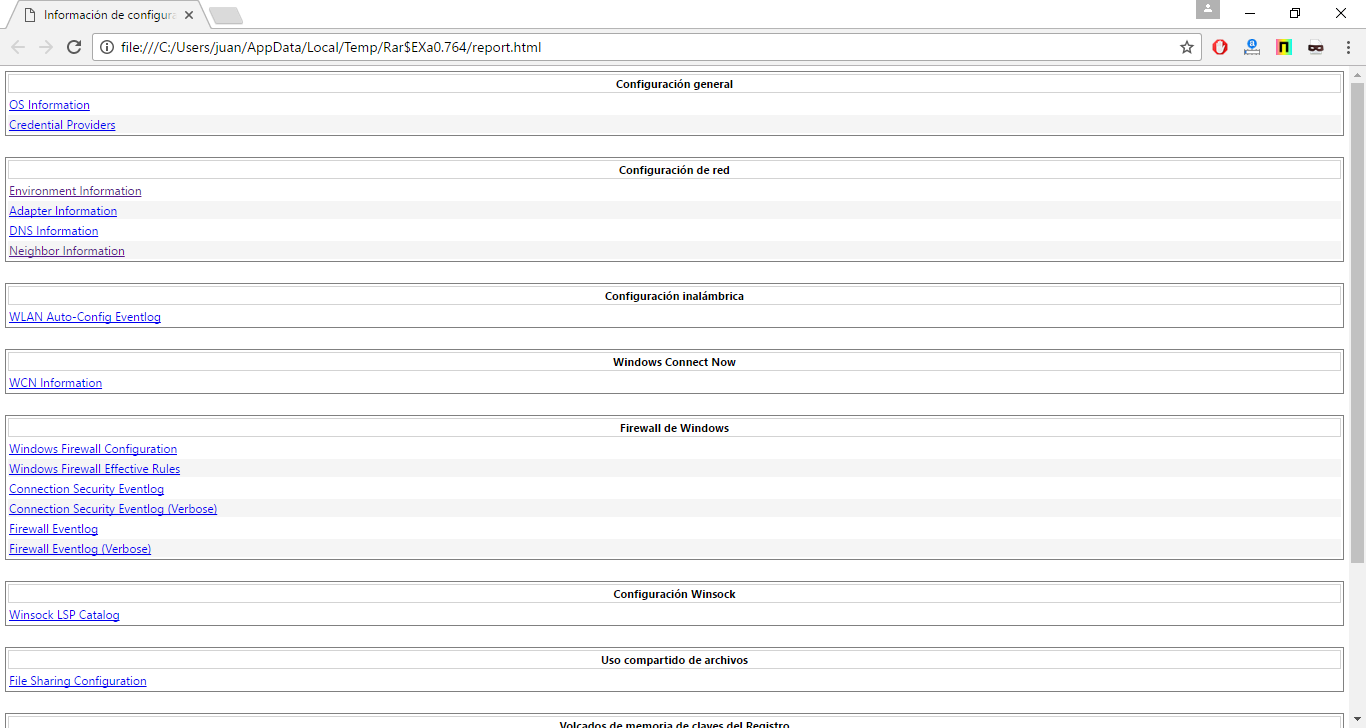
Y se obtienen los siguientes ficheros:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 |
adapterinfo.txt allcred.reg.txt allcredfilter.reg.txt apiperm.reg.txt application_export.evtx application_export_3082.mta battery-report.html createbindingmap.log dispdiag_start.dat dispdiag_stop.dat dns.txt dxdiag.txt envinfo.txt filesharing.txt gpresult.txt hklmwlansvc.reg.txt homegrouplistener.reg homegroupprovider.reg hotfixinfo.log neighbors.txt netevents.xml neteventslog.txt netiostate.txt networkprofiles.reg.txt notif.reg.txt osinfo.txt policymanager.reg powershellinfo.log processes.txt report.etl report.html scm.evm.1 scm.evm.2 scm.evm.3 serviceinfo.log sysports.xml sysportslog.txt system_export.evtx system_export_3082.mta vmswitchlog.evtx vmswitchlog_3082.mta wcmlog.evtx wcmlog_3082.mta wcninfo.txt wfpfilters.xml wfplog.log wfpstate.xml wfpstatelog.txt windowsfirewallconfig.txt windowsfirewallconseclog.evtx windowsfirewallconseclogverbose.evtx windowsfirewallconseclogverbose_3082.mta windowsfirewallconseclog_3082.mta windowsfirewalleffectiverules.txt windowsfirewalllog.evtx windowsfirewalllogverbose.evtx windowsfirewalllogverbose_3082.mta windowsfirewalllog_3082.mta windows_panther_setupact.log windows_panther_setuperr.log winsock.log winsockcatalog.txt wlan-report-2017-05-06.html wlan-report-latest.cab wlan-report-latest.html wlan-report-latest.xml wlanautoconfiglog.evtx wlanautoconfiglog_3082.mta wlaninfo.txt wwanlog.evtx wwanlog_3082.mta |