VÍDEOS
«
1
/
71
»
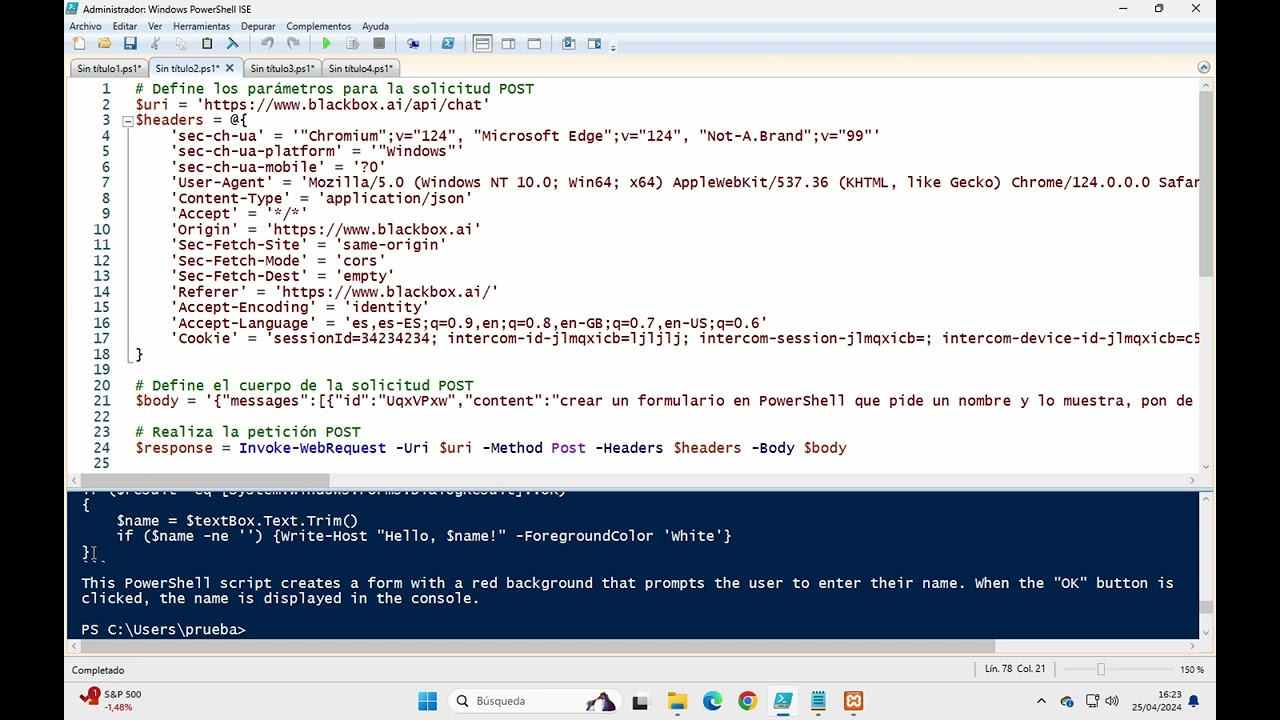
Crear código de PowerShell automatizando un LLM (gratis y sin pagar API)
Utilizar sesiones de las aplicaciones web en PowerShell
Transcribir un archivo de audio a texto utilizando la biblioteca SpeechRecognition de Python
«
1
/
71
»
CURSOS
PUBLICACIONES DIARIAS
LO ÚLTIMO
- Invitar o conectarte con gente de forma masiva en LinkedIn con JavaScript (marzo 2024) 23/04/2024
- Protegido: Curso online de PowerShell (abril 2024) 22/04/2024
- Conversor de voz a texto utilizando webkitSpeechRecognition en JavaScript 18/04/2024
- Crear un grabador de audio en el navegador web con JavaScript 18/04/2024
- Transcribir un archivo de audio a texto utilizando la biblioteca SpeechRecognition de Python 18/04/2024
- API de FastAPI para mostrar procesos en ejecución con Python (desplegar en Vercel) 16/04/2024
- Dibujo simple en JavaScript utilizando el elemento canvas en HTML5 16/04/2024
- Trace metadata processing, parameter binding, and an expression 16/04/2024
- Predicción de clasificación de imágenes con MobileNetV2 15/04/2024

 Suscribirse al canal
Suscribirse al canal